Building a base of cybersecurity experts in Indiana - WISH-TV | Indianapolis News | Indiana Weather | Indiana Traffic
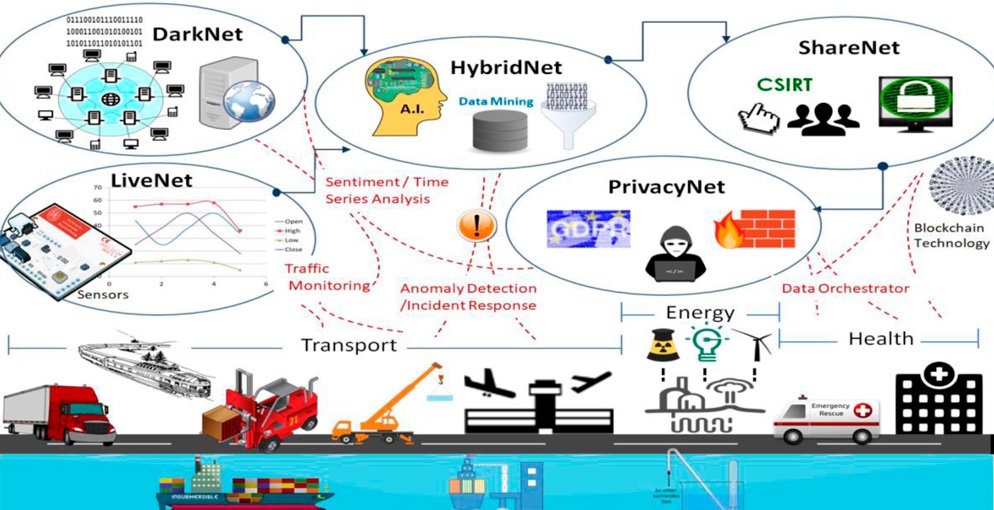
CYBERSANE - CYBER SECURITY INCIDENT HANDLING, WARNING AND RESPONSE SYSTEM FOR THE EUROPEAN CRITICAL INFRASTRUCTURES - Fundación Valenciaport

Cyber Security System Technology Icons Set Vector. Cyber Security Software And Application, Padlock And Password For Data Base And Information Protection From Virus Line. Color Illustrations Stock Vector | Adobe Stock

Inside the British military base where young hackers learn to stop cybercrime | UK security and counter-terrorism | The Guardian